
This first part will define core concepts, explaining the history of blockchain technology, and provide a brief overview of identity management solutions based on this transformative technology.
The History of Blockchain Technology
The idea for the blockchain has its roots in multiple concepts. In 1991 and 1992, Stuart Haber and W. Scott Stornetta designed a system that could link documents together. These documents became tamper-proof, and their timestamps could no longer be modified.
They achieved this using Merkle trees. A Merkel tree is a hierarchical data structure where parent nodes contain the hash of their children nodes.
The current blockchain implementations also borrowed ideas from the Hashcash proof-of-work system. Adam Back used this system in 1997 as a way to fight email spam. In his system, an email sender has to perform a computational process before sending a message. This process consists of hashing the email in a way that the hash starts with a defined number of leading zeros.
How does this system work? Here’s an example:
- The email sender first hashes his message and checks if the generated hash starts with the correct number of leading zeros.
- If that isn’t the case, the sender modifies a parameter in the message’s header and hashes the message again. Remember, modifying the message’s header modifies the generated hash.
- The sender has to hash his message and modify the header parameter until he is able to generate a hash that starts with the correct number of leading zeros.
This process leads to additional work for message senders. Since it’s easy to confirm that a specific message with a certain header generates a particular hash, it’s easy to verify that the sender has completed the requested work.
General Principles of Blockchain Technology
The first implementation of a blockchain was proposed in 2008 by Satoshi Nakamoto through the Bitcoin cryptocurrency. Satoshi’s true identity is unknown to this day, and the name could likely be a pseudonym or a group of people.
But why was the creation of Bitcoin so important? The goal of Bitcoin is to provide a decentralized currency that isn’t governed by a central authority. It also demonstrated the mainstream practicality of blockchain technology.
The different blockchains in use today are built on the same general principles. So, let’s simplify some of these core blockchain principles and why they are even important in the first place.
- Blockchains work by exchanging value. In the case of Bitcoin, the value is the Bitcoin currency.
- Bitcoin’s blockchain acts as a ledger. This ledger records every Bitcoin currency transaction between people. The ledger is organized in blocks and each block contains a specific number of transactions.
- The ledger is distributed. Every node taking part in the Bitcoin network has a copy.
- Blocks are organized in a tamper-proof hierarchical structure. A child block is hashed and contains the hash of its parent. It’s impossible to modify a block because the transactions that it contains a link to the parent block without modifying the block’s hash. Both the content of the chain of blocks and the links between the blocks are immutable.
- A block’s hash is actually a proof-of-work. In Bitcoin jargon, the process of calculating the proof-of-work is called mining. It involves the following steps:
- A Bitcoin currency transaction occurs between two parties. The transaction is broadcasted to all the nodes on the bitcoin network.
- Transactions are recorded. Once a certain number of new transactions have been broadcasted, they are organized into a block.
- Every participating node in the Bitcoin network then tries to hash the block with a nonce. When fed in the hashing algorithm, the nonce has to generate a hash that starts with a certain number of leading zeros. Finding the correct nonce is the “work,” while the proof-of-work is the block’s hash.
- In the Bitcoin system, the first node that is able to broadcast the proof-of-work is awarded a certain number of Bitcoins. The “winning” node actually awards itself Bitcoins by adding a transaction to the block that has calculated the hash. The number of Bitcoins that are awarded decreases over time. However, There is a fixed number of Bitcoins—with 21 million being the maximum that will ever be awarded. As we get closer to that number, fewer Bitcoins will be awarded to “winning” nodes.
Here is a graphical representation of how blocks are chained together with their hash.
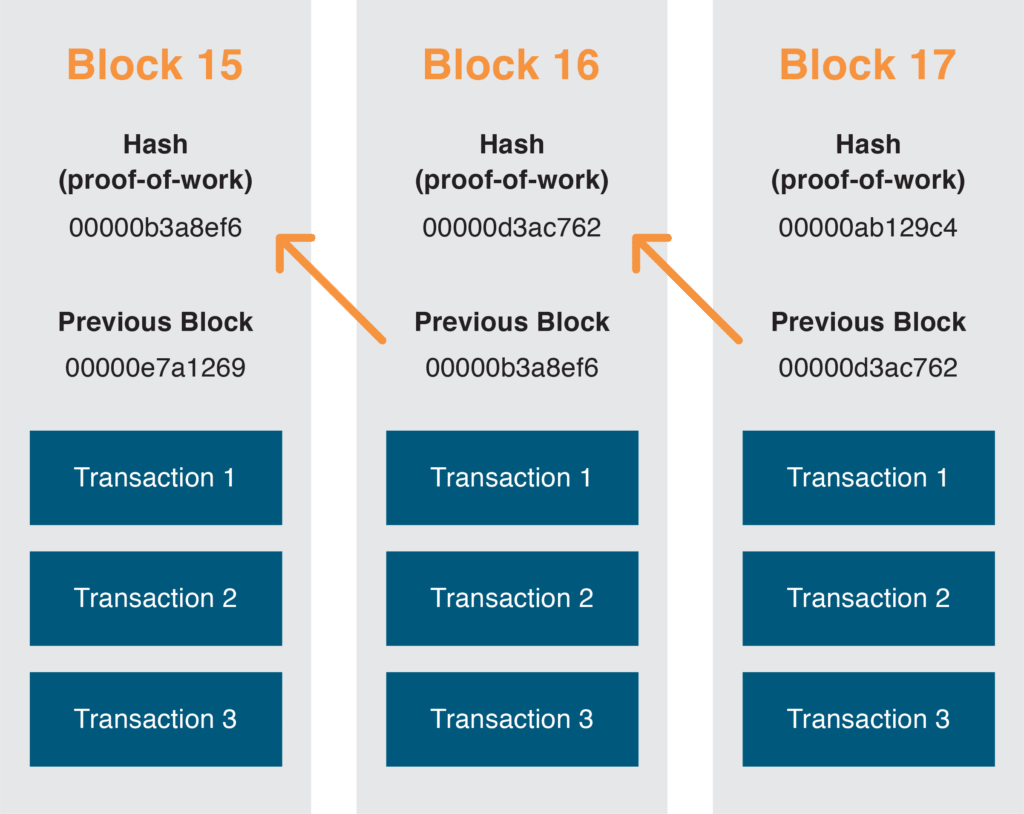
The Bitcoin system offers a distributed value exchange platform by implementing these concepts. The value exchanged is the Bitcoin currency.
The blockchain on which Bitcoin is founded uses a cryptography-based technique to ensure that the transactions it hosts are accurate and tamper-proof. The system’s users do not need to rely on a trusted third-party to ensure the validity of the distributed ledger.
There is also no need for a third-party to inject currency into the system. As described earlier, new Bitcoins are automatically injected in the system at a defined rate.
Bitcoin was the first cryptocurrency to be legitimized through acceptance by many retailers, the creation of futures contracts in the financial markets, and more. It is now accepted by multiple service providers, is often used to buy goods, and can be exchanged for fiat currencies.
Blockchain technology is useful for currencies that do not require centralized management. And as this technology evolves, new industries are starting to look into its applications.
Identity Management Use Cases
Blockchain can also be used for identity management purposes. The idea of storing an identity on a distributed blockchain can be applicable to many use cases and can solve a host of problems.
There are already a couple of identity management systems built on a blockchain. However, since the concepts are relatively new, the majority of these systems are still in a design or pilot stage. Here are a few examples of identity management systems designed for these situations.
Identity Information Protection
In today’s digital age, identity theft is a major issue. In 2017, 16.7 million people in the U.S. were victims of identity fraud. In total, $16.8 billion have been lost through fraud.
Service providers have to store a lot of personally identifiable information. A security breach in their infrastructure can be a goldmine for fraudsters. It’s much easier to target fewer entities than it is to steal data stored in a distributed fashion.
An identity management system built using the blockchain can be beneficial for both service providers and consumers. First, storing identities on a blockchain instead of a service provider’s servers reduces liability. In cases of identity theft:
- The service provider cannot be held responsible.
- Their reputation is safe.
- They cannot become victims of extortion themselves.
- They do not have to spend resources to secure their identity management system.
A system like this also offers additional benefits to consumers. Identity information is controlled by consumers and not the service providers themselves. This assures consumers that their data is not used or sold without their consent.
There are even identity management systems that allow information to be verified without sharing the specific information itself. This was demonstrated at the 2018 Consensus Conference when the Civic blockchain identity management system partnered with Budweiser to provide a vending machine for beer.
Users could use the Civic app to order a beer if they were over 21 years old. The app used a zero-knowledge proof algorithm to tell the vending machine that the customer was over 21 without revealing its exact age.
Helping Refugees
A trusted and decentralized identity management system built using the blockchain can solve problems in a more efficient way than standard solutions. Refugees can benefit from this kind of identity management system too. Blockchain-based solutions have been designed to address their specific needs.
A refugee generally does not have proof of their identity. They may have legal documents issued by their country of origin, but these documents may not be valid or reliable. Proof of identity services pose a major problem for refugees.
For example, one of these services is the UN’s World Food Program that distributes money so refugees can purchase food. This money has to get into the right person’s hands without being intercepted along the way. Traditional solutions would involve a third party acting as an intermediate between refugees and food stores to keep track of transactions. However, third parties are not always trustworthy. It would be better if the UN could distribute the money directly, without going through a third party at all.
That is exactly what the World Food Program is doing with its Building Blocks pilot initiative, which is currently active in a Jordanian refugee camp. When a Syrian refugee arrives in the camp, they are given an identity using the blockchain. This identity is registered along with biometric information about the refugee. The refugee can then go to a food store, where the transaction can be authenticated with the refugee’s blockchain identity. The food store can then turn to the World Food Program with proof of the transaction and seek reimbursement.
Over time, the blockchain identity becomes associated with additional transactions and government-issued documents, becoming increasingly reliable. At a certain point, the identity becomes trustworthy enough that a bank would be willing to open an account for the refugee and give them a loan.
Augmenting an identity with more information through usage is not limited to blockchain systems targeting refugees. There are at least two other systems that are gaining traction that use these features, and these systems are designed for a more mainstream audience.
There is Civic, the system mentioned earlier in the beer vending machine proof-of-concept, and there is Persona, a system currently being developed, which is available today with a limited feature set.
What’s Next for the Blockchain? A Deeper Dive Into Identity Management.
Now you understand the basic history and applications of blockchain technology. While this transformative technology went mainstream with Bitcoin, it won’t be long before major financial institutions, shipping companies, and other data-heavy industries turn to blockchain technology to safeguard sensitive information.
In our next post, we’ll take a more in-depth look into how blockchain technology is driving innovation in identity management systems.
Sources
- 2018 Identity Fraud: Fraud Enters a New Era of Complexity | Javelin – https://www.javelinstrategy.com/coverage-area/2018-identity-fraud-fraud-e nters-new-era-complexity
- Blockchain – Wikipedia – https://en.wikipedia.org/wiki/Blockchain
- Blockchain Technology Explained (2 Hour Course) https://www.youtube.com/watch?v=qOVAbKKSH10 Building Blocks | WFP Innovation – https://innovation.wfp.org/project/building-blocks
- Civic Secure Identity Ecosystem – Decentralized Identity & Reusable KYC – https://www.civic.com/
- Cryptobeer vending machine promises blockchain-enabled benders – https://mashable.com/2018/05/15/cryptobeer-vending-machine-consensus/
- Identity – Take Control Of Your Personal Data – Persona, Civic – com – https://podcast.bitcoin.com/e79-Identity-Take-Control-Of-Your-Pers onal-Data-Persona-Civic
- Persona – https://persona.im/
- Proof-of-work system – Wikipedia – https://en.wikipedia.org/wiki/Proof-of-work_system





